Running a node can be a highly profitable venture in the world of blockchain. Whether you’re operating a validator node on Ethereum, a masternode for DASH, or a Flux infrastructure node, security is non-negotiable. With rewards on the line and uptime being crucial, protecting your node from hackers and avoiding downtime is key to long-term success.
Why Node Security Matters
Your node is not just a passive machine—it’s a vital part of the blockchain network. If compromised, attackers can:
- Steal your staked tokens or rewards
- Gain unauthorized access to sensitive data
- Cause penalties or slashing (especially in PoS networks)
- Damage your network reputation or reduce your earnings
And if your node goes offline, you may lose daily rewards or worse, be kicked out of validator sets altogether.
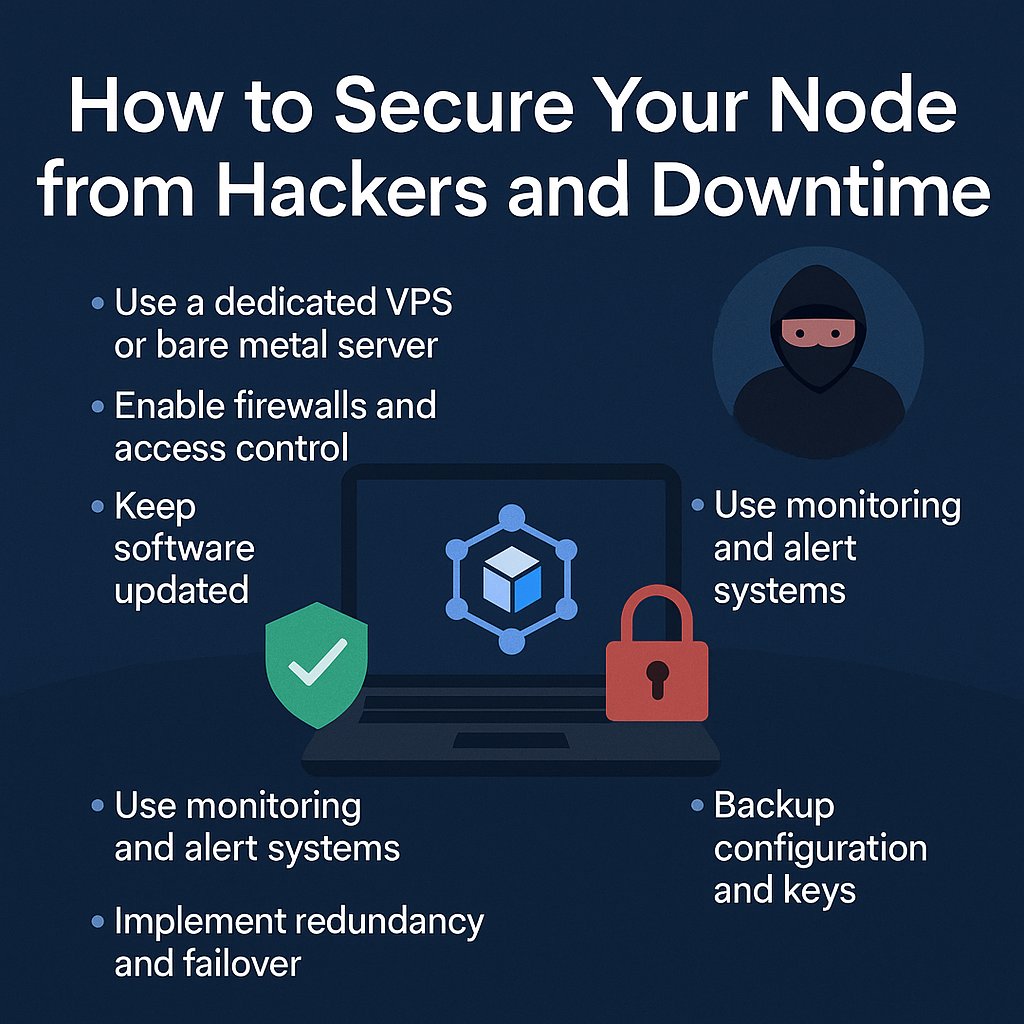
Essential Security Tips for Protecting Your Node
1. Use a Dedicated VPS or Bare Metal Server
Running your node on shared hosting is a major risk. Always opt for:
- A Virtual Private Server (VPS) with isolated resources
- A bare metal server for ultimate performance and control
- Cloud platforms with built-in DDoS protection (like AWS, Contabo, or DigitalOcean)
2. Enable Firewalls and Access Control
Use a firewall to only allow essential ports (e.g., SSH, node-specific ports) and block everything else.
Recommended tools:
- UFW (Uncomplicated Firewall) on Linux
- Fail2ban to block repeated login attempts
- Cloudflare Tunnel for external node interfaces
Restrict access to your server using:
- IP whitelisting
- Non-root user accounts
- Public-key authentication instead of passwords
3. Keep Software Updated
Outdated software is a hacker’s best friend. Always keep:
- Node client versions up to date
- OS and security patches installed
- Dependencies like Docker, Nginx, etc., regularly maintained
Use automation tools like Watchtower to auto-update Docker containers securely.
4. Use Monitoring and Alert Systems
Downtime = lost income. Install monitoring tools like:
- Grafana + Prometheus for performance tracking
- Uptime Kuma, NodeWatch, or Zabbix for live alerts
- Enable email or Telegram notifications for immediate action
5. Backup Your Configuration and Keys
Make regular, encrypted backups of:
- Wallets or keystore files
- Node configurations
- Certificates and credentials
Store backups on a separate cloud storage or physical drive. If your node crashes or gets compromised, you can recover quickly.
6. Implement Redundancy and Failover
Use a failover node setup or load balancer to keep your node online even if your main server goes down. You can:
- Run a hot standby replica
- Use DNS failover (e.g., Cloudflare)
- Use multi-region deployment for critical infrastructure
Tools to Secure Your Node Infrastructure
| Tool/Service | Purpose |
|---|---|
| UFW / iptables | Basic firewall setup |
| Fail2Ban | Brute-force protection |
| CrowdSec | Collaborative threat detection |
| Watchtower | Auto Docker updates |
| Uptime Kuma | Uptime monitoring |
| Grafana + Prometheus | Performance metrics |
| AWS Shield / Cloudflare | DDoS Protection |
Common Mistakes to Avoid
- Using root access for node operations
- Running nodes on a personal or home network
- Ignoring port exposure
- Not setting up 2FA on hosting control panels
- Skipping backups or never testing recovery
Final Thoughts
Your node is your revenue stream. Securing it is not optional—it’s critical. Whether you’re an individual operator or managing an institutional node setup, taking proactive security steps will help you stay online, safe, and profitable.
In a decentralized world, the responsibility is yours. Harden your infrastructure, stay vigilant, and you’ll reap consistent rewards while avoiding costly downtime or attacks.
Stop Selling Promises — It’s Time To Show More Proof
Why Institutional Investors Are Turning to Node-Based Income